Mitigating Cybersecurity Risks with Enterprise eSIM Policies
Enterprise eSIM policies help organizations secure mobile connectivity by eliminating SIM based risks, improving visibility, and enabling centralized, policy driven control across global teams and devices.

Digital transformation has reshaped how enterprises connect people, devices, applications, and data. Mobility is no longer a supporting function. It is a core business capability. Employees work across borders, cloud applications span regions, and devices connect from virtually anywhere. While this flexibility unlocks productivity and scale, it also expands the attack surface that cybercriminals actively target.
Connectivity is often overlooked in cybersecurity strategies. Firewalls, endpoint protection, and identity management receive significant attention, yet the mobile network layer remains a frequent weak point. Traditional SIM cards, unmanaged roaming, shadow IT usage, and fragmented telecom contracts create visibility gaps that attackers exploit.
Enterprise eSIM policies address these risks at their foundation. By replacing physical SIM dependencies with centralized, software driven connectivity control, organizations can significantly reduce exposure, improve compliance, and strengthen security posture across their mobile ecosystem.
This blog explores in depth how enterprise eSIM policies mitigate cybersecurity risks, why they matter in modern threat landscapes, and how organizations can implement them effectively using platforms like Voye Data Pool.
The Evolving Cybersecurity Threat Landscape for Mobile Enterprises
Enterprises today face a radically different threat environment than they did even five years ago. The convergence of cloud, mobile, and remote work has blurred traditional network perimeters.
Employees now access sensitive systems from airports, hotels, shared workspaces, and home networks. Corporate data travels across public networks and multiple jurisdictions. Meanwhile, attackers have adapted with techniques designed to exploit mobility.
Mobile focused threats include SIM swapping, rogue base stations, insecure roaming networks, and data interception through compromised carriers. Phishing campaigns increasingly target mobile devices where users are more likely to click links or approve prompts quickly. Malware designed for mobile operating systems continues to grow in sophistication.
Traditional connectivity models struggle to keep pace with this reality. Physical SIM cards are difficult to track, replace, or revoke quickly. Roaming agreements vary in security standards. IT teams often lack real time visibility into which devices are connected, where they are located, or how data is being used.
This is where enterprise eSIM policies become a strategic security control rather than a mere connectivity upgrade.
Understanding eSIM Technology in an Enterprise Context
An eSIM, or embedded SIM, is a programmable SIM integrated directly into a device. Unlike physical SIM cards, eSIM profiles can be remotely provisioned, updated, suspended, or deleted without physical access to the device.
In an enterprise context, eSIM technology enables centralized control over mobile connectivity across smartphones, tablets, laptops, and IoT devices. IT teams can manage thousands of connections from a single platform, applying consistent policies regardless of geography or device type.
Enterprise eSIM platforms go beyond basic provisioning. They integrate monitoring, analytics, security controls, and automation that align with broader IT and cybersecurity frameworks.
The security value of eSIM lies not just in its form factor, but in the policy driven management layer that surrounds it.

Simplify Enterprise Mobile Security
Centralize, secure, and scale eSIM connectivity for teams
Why Traditional SIM Based Connectivity Increases Cyber Risk
To appreciate the value of enterprise eSIM policies, it is important to understand the limitations and risks associated with traditional SIM based connectivity.
Physical SIM cards are easy to lose, steal, clone, or misuse. When an employee leaves the organization or loses a device, deactivating a physical SIM often involves delays, manual processes, and coordination with external carriers. During this window, unauthorized access can occur.
Roaming adds another layer of complexity. When devices roam internationally, they connect to partner networks with varying security standards. Enterprises often lack visibility into these networks and cannot enforce consistent policies across them.
Shadow IT further compounds the problem. Employees frequently purchase local SIMs while traveling to reduce costs or improve coverage. These unmanaged connections bypass corporate controls entirely, creating blind spots for security teams.
Billing fragmentation also impacts security. Multiple carrier contracts across regions make it difficult to monitor usage patterns and detect anomalies that may indicate compromise or misuse.
Enterprise eSIM policies directly address these challenges by centralizing control and eliminating reliance on physical SIM logistics.
Core Cybersecurity Risks Mitigated by Enterprise eSIM Policies
Unauthorized Network Access
Unauthorized access is a leading cause of data breaches. Physical SIM cards can be inserted into unauthorized devices, shared between users, or exploited through SIM swap attacks.
Enterprise eSIM policies bind connectivity profiles to specific devices and users. Activation requires authentication and approval through a secure platform. If a device is compromised or lost, connectivity can be revoked instantly from a central dashboard.
This reduces the risk of attackers gaining network access through stolen or misused SIMs.
Data Interception and Man in the Middle Attacks
Mobile data interception remains a significant threat, especially in regions with less secure telecom infrastructure. Rogue base stations and compromised networks can intercept unencrypted traffic or manipulate connections.
Enterprise eSIM platforms allow organizations to select trusted carrier networks and enforce secure routing policies. Some platforms integrate with private APNs and VPNs to ensure that mobile traffic is encrypted end to end.
By controlling which networks devices can connect to, enterprises reduce exposure to high risk carriers and regions.
Shadow IT and Unmanaged Connectivity
Shadow IT is not limited to software applications. Unmanaged connectivity is equally dangerous. Employees using personal SIMs or local prepaid plans create invisible access paths into corporate systems.
Enterprise eSIM policies eliminate the need for personal SIM purchases. Employees receive reliable global connectivity that works across borders without roaming surprises. IT retains full visibility and control over usage.
This visibility enables security teams to detect unusual patterns, such as excessive data usage or connections from unexpected locations.
Delayed Incident Response
Speed matters in cybersecurity. The longer a compromised device remains connected, the greater the potential damage.
With traditional SIMs, deactivation often requires manual carrier interaction. With enterprise eSIM policies, IT teams can suspend or delete profiles in seconds. This rapid response capability significantly limits attack dwell time.
eSIM Policies as a Pillar of Zero Trust Architecture
Zero Trust security models assume that no device, user, or network is inherently trustworthy. Every connection must be verified continuously.
Enterprise eSIM policies align naturally with Zero Trust principles. Each eSIM profile represents a controlled identity at the network layer. Access can be granted based on device compliance, user role, location, and time.
Connectivity becomes conditional rather than implicit. A device that falls out of compliance can automatically lose network access until issues are resolved.
This integration of connectivity into Zero Trust frameworks closes a gap that many organizations overlook.
Centralized Visibility and Monitoring for Security Teams
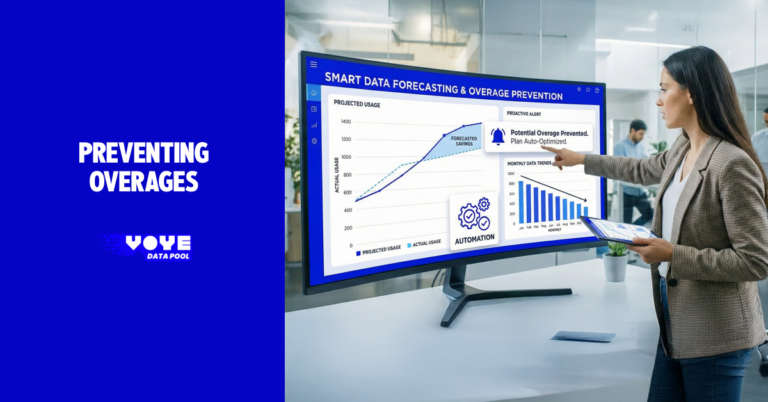
One of the most powerful benefits of enterprise eSIM management is centralized visibility. Security teams gain real time insight into all active connections, data usage, locations, and network performance.
This visibility supports proactive threat detection. Sudden spikes in data usage may indicate malware activity. Connections from unexpected regions may signal credential compromise or device theft.
Advanced platforms like Voye Data Pool provide analytics and alerts that integrate with existing security operations workflows. Instead of reacting after a breach, teams can identify and address risks early.
Secure Global Connectivity Without Roaming Vulnerabilities
Global operations introduce unique security challenges. Roaming agreements vary widely in terms of network security, lawful interception practices, and infrastructure maturity.
Enterprise eSIM platforms simplify global connectivity by providing a unified profile that works across multiple regions without traditional roaming dependencies. Devices connect to the best available local network while maintaining enterprise level security controls.
Policies can restrict connectivity in high risk regions or require additional authentication steps. This ensures that global mobility does not come at the expense of security.
Policy Driven Lifecycle Management of Devices
Device lifecycle management is critical to cybersecurity. From onboarding to decommissioning, each stage presents risks if not handled properly.
Enterprise eSIM policies enable automated lifecycle workflows. When a new employee joins, connectivity can be provisioned securely before the device is shipped. When an employee leaves, connectivity can be revoked immediately, regardless of device location.
For IoT deployments, lifecycle management is even more critical. Devices may be deployed in remote or hostile environments where physical access is limited. eSIM enables remote control throughout the device lifespan, reducing the risk of orphaned or compromised connections.
Compliance and Regulatory Benefits of eSIM Policies
Regulatory compliance is closely tied to cybersecurity. Data protection regulations such as GDPR and industry specific standards require organizations to demonstrate control over data access and transmission.
Enterprise eSIM policies support compliance by providing auditable logs of connectivity activity. Organizations can demonstrate who had access, when, and from where.
Centralized management also simplifies compliance across jurisdictions. Instead of navigating dozens of local carrier contracts, enterprises maintain a single policy framework that adapts to regional requirements.
This consistency reduces compliance risk and simplifies audits.
Reducing Human Error Through Automation
Human error remains one of the leading causes of security incidents. Manual SIM management, ad hoc roaming approvals, and inconsistent deactivation processes create opportunities for mistakes.
Enterprise eSIM platforms automate many of these tasks. Policies enforce consistency, while workflows reduce reliance on manual intervention.
Automation ensures that security best practices are applied uniformly, regardless of scale. Whether managing ten devices or ten thousand, the same controls apply.
Integrating eSIM Management with Enterprise Security Stacks
Enterprise eSIM policies are most effective when integrated with broader security and IT systems. Identity management, endpoint security, and mobile device management platforms all benefit from shared data.
For example, if an endpoint security solution detects malware on a device, the eSIM platform can automatically suspend connectivity. If an identity system flags suspicious login behavior, connectivity can be restricted until verification is complete.
This integration creates a feedback loop that strengthens overall security posture.
The Role of Trusted Standards and Industry Bodies
Enterprise eSIM technology is supported by global standards that ensure interoperability and security. Organizations such as GSMA define specifications for eSIM provisioning, authentication, and lifecycle management.
By leveraging standards based platforms, enterprises reduce the risk of vendor lock in and ensure compatibility with a wide range of devices and networks.
Standards also provide assurance that security controls meet industry accepted benchmarks.
Case Scenarios Where Enterprise eSIM Policies Prevent Breaches
Consider a traveling executive whose smartphone is stolen at an airport. With a physical SIM, the device may remain connected for hours or days until the loss is reported and processed. During this time, attackers could access email, cloud applications, and corporate data.
With enterprise eSIM policies, the device can be immediately disconnected remotely. The eSIM profile is deleted, cutting off network access regardless of physical possession.
In another scenario, an IoT sensor deployed in a remote facility begins transmitting unusually high volumes of data. Centralized monitoring flags the anomaly, and connectivity is suspended pending investigation. A potential breach is contained before data exfiltration escalates.
These scenarios illustrate how connectivity control directly impacts security outcomes.
Addressing Cost Concerns Without Sacrificing Security
Security investments often face scrutiny due to perceived costs. Enterprise eSIM policies deliver both security and financial benefits.
By consolidating connectivity under a single platform, organizations reduce roaming fees, eliminate redundant contracts, and gain predictable pricing. Cost transparency supports better budgeting and reduces pressure to cut corners that compromise security.
Employees no longer need to seek cheaper local SIMs, which often introduce unmanaged risks. Instead, they receive reliable, secure connectivity that supports productivity and compliance.
Building a Culture of Secure Mobility
Technology alone cannot solve cybersecurity challenges. Policies, training, and culture play equally important roles.
Enterprise eSIM policies support a culture of secure mobility by removing friction. When secure connectivity is easy and reliable, employees are less likely to bypass controls.
Clear policies around device usage, travel connectivity, and incident reporting reinforce the technical controls provided by eSIM platforms.
Over time, secure mobility becomes the default rather than an exception.
Why Voye Data Pool Aligns with Enterprise Security Goals
Voye Data Pool is built for enterprises that view connectivity as a strategic asset rather than a commodity. The platform simplifies, scales, and secures business connectivity through advanced eSIM management.
From global teams to IoT deployments, Voye Data Pool provides centralized activation, monitoring, and control from a single secure platform. Enterprises gain reliable, borderless connectivity without sacrificing visibility or security.
The platform supports policy driven management that aligns with Zero Trust principles, regulatory requirements, and modern security operations. By integrating connectivity into the broader security strategy, organizations close a critical gap that attackers often exploit.
Implementing Enterprise eSIM Policies Successfully
Successful implementation begins with clear objectives. Organizations should assess their current connectivity risks, identify gaps in visibility and control, and define security requirements.
Pilot programs allow teams to test eSIM policies with a subset of users or devices. Feedback from these pilots informs broader rollout strategies.
Collaboration between IT, security, procurement, and compliance teams ensures alignment. Connectivity touches multiple functions, and shared ownership improves outcomes.
Ongoing monitoring and policy refinement are essential. Threat landscapes evolve, and eSIM policies should adapt accordingly.
The Future of Secure Enterprise Connectivity
As enterprises continue to embrace remote work, IoT, and global expansion, the importance of secure connectivity will only increase. Attackers will continue to target the weakest links, and unmanaged mobile networks remain a prime target.
Enterprise eSIM policies represent a foundational shift in how organizations approach connectivity and security. By embedding control, visibility, and automation at the network layer, enterprises reduce risk while enabling agility.
Platforms like Voye Data Pool demonstrate that security and simplicity are not mutually exclusive. With the right policies and tools, organizations can achieve reliable, scalable, and secure connectivity that supports both business growth and cybersecurity resilience.
In a world where every device is a potential entry point, controlling how those devices connect is no longer optional. Enterprise eSIM policies are not just a connectivity upgrade. They are a critical component of modern cybersecurity strategy.

Enterprise Connectivity Made Secure
Manage, monitor, and protect employee eSIM connectivity worldwide



 12 min read
12 min read